🚨 BOLO: Samsung Budget Phones Contain Pre-Installed Data-Harvesting Software: Critical Action Steps for Legal Professionals
/‼️ ALERT: Hidden Spyware in Samsung Phones!
Samsung Galaxy A, M, and F series smartphones contain pre-installed software called AppCloud, developed by ironSource (now owned by Unity Technologies), that harvests user data, including location information, app usage patterns, IP addresses, and potentially biometric data. This software cannot be fully uninstalled without voiding your device warranty, and it operates without accessible privacy policies or explicit consent mechanisms. Legal professionals using these devices face significant risks to attorney-client privilege and confidential client information.
The Threat Landscape
AppCloud runs quietly in the background with permissions to access network connections, download files without notification, and prevent phones from sleeping. The application is deeply integrated into Samsung's One UI operating system, making it impossible to fully remove through standard methods. Users across West Asia, North Africa, Europe, and South Asia report that even after disabling the application, it reappears following system updates.
The digital rights organization SMEX documented that AppCloud's privacy policy is not accessible online, and the application does not present users with consent screens or terms of service disclosures. This lack of transparency raises serious ethical and legal compliance concerns, particularly for attorneys bound by professional responsibility rules regarding client confidentiality.
Legal and Ethical Implications for Attorneys
Under ABA Model Rule 1.6, attorneys must make "reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client". The duty of technological competence under Rule 1.1, Comment 8, requires attorneys to "keep abreast of changes in the law and its practice, including the benefits and risks associated with relevant technology".
The New York Bar's 2022 ethics opinion specifically addresses smartphone security, prohibiting attorneys from sharing contact information with smartphone applications unless they can confirm that no person will view confidential client information and that data will not be transferred to third parties without client consent. AppCloud's data harvesting practices appear to violate both conditions.
Immediate Action Steps
‼️ Act now if you’ve purchased certain samsung phones - your bar license could be in jeopardy!
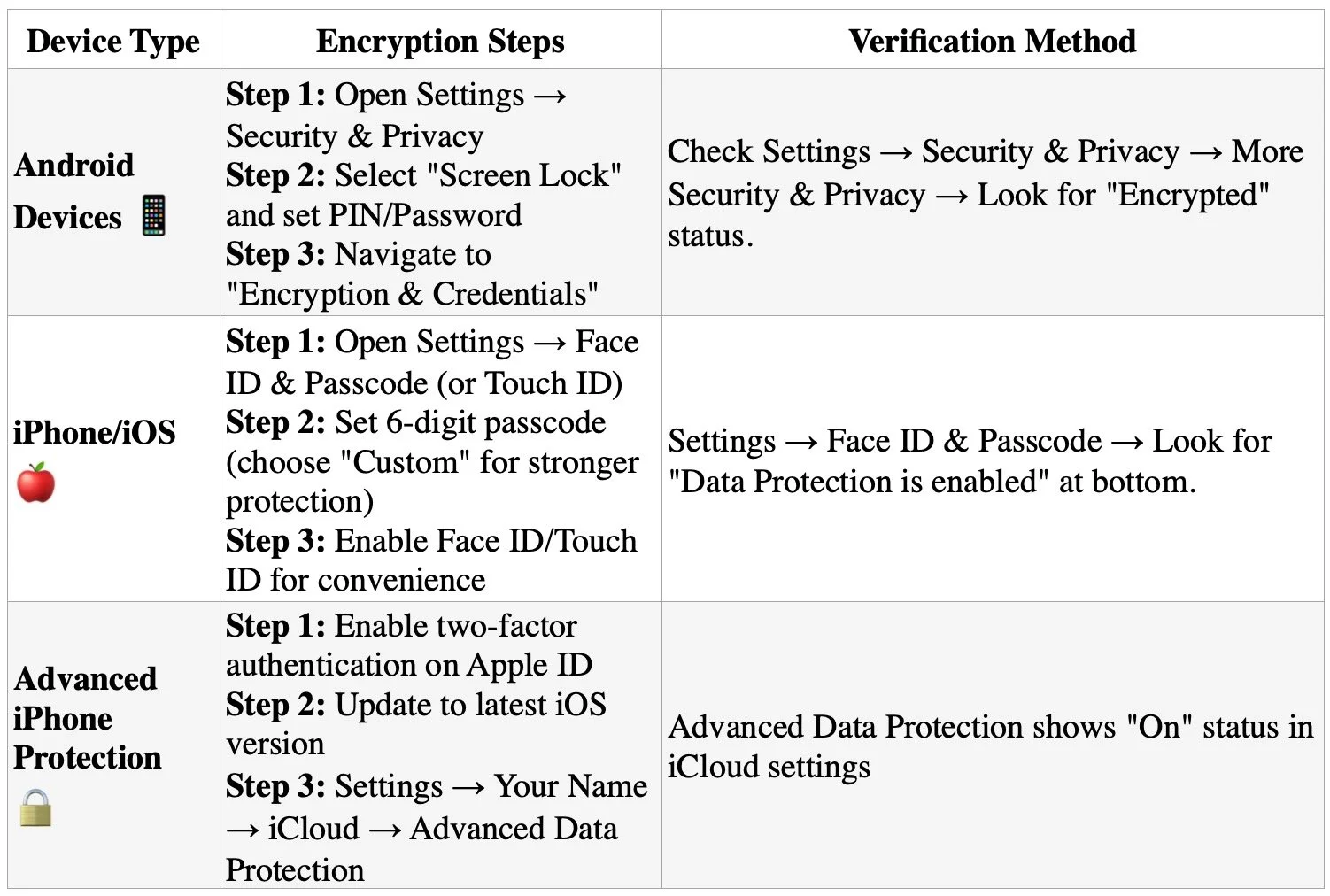
Step 1: Identify Affected Devices
Check whether you use a Samsung Galaxy A series (A05 through A56), M series (M01 through M56), or F series device. These budget and mid-range models are primary targets for AppCloud installation.
Step 2: Disable AppCloud
Navigate to Settings > Apps > Show System Apps > AppCloud > Disable. Additionally, revoke notification permissions, restrict background data usage, and disable the "Install unknown apps" permission.
Step 3: Monitor for Reactivation
After system updates, return to AppCloud settings and re-disable the application.
Step 4: Consider Device Migration
For attorneys handling highly sensitive matters, consider transitioning to devices without pre-installed data collection software. Document your decision-making process as evidence of reasonable security measures.
Step 5: Client Notification Assessment
Evaluate whether client notification is required under your jurisdiction's professional responsibility rules. California's Formal Opinion 2020-203 addresses obligations following an electronic data compromise.
The Bottom Line
Budget smartphone economics should not compromise attorney-client privilege. Samsung's partnership with ironSource places aggressive advertising technology on devices used by legal professionals worldwide. Until Samsung provides transparent opt-out mechanisms or removes AppCloud entirely, attorneys using affected devices should implement immediate mitigation measures and document their security protocols.